Are industrial enterprises prepared with an OT-centric recovery plan?
- Anna Ribeiro
- Dec 4, 2022
- 6 min read
Updated: Dec 5, 2022
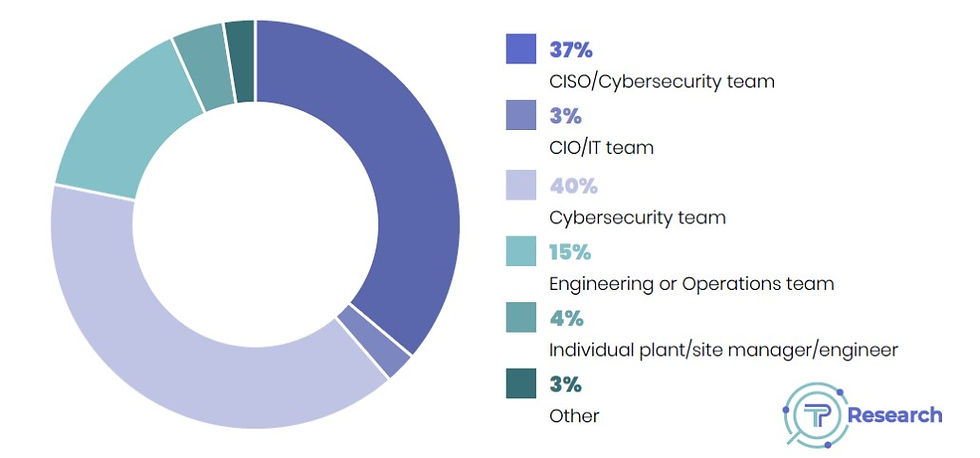
A survey report published today in Industrial Cyber Magazine released details findings of an overwhelming 90% of respondents disclosing that the OT (operational technology) recovery process should be owned by OT professionals and not by IT, due to the considerable differences between OT and IT environments in the OT/ICS recovery process.
Additionally, the TPR Survey Report disclosed that 40 percent of respondents revealed that the recovery process in their organization is owned by IT teams. This dissonance may be putting OT systems at risk for costly downtime following an attack.
“While current IT and cloud-based solutions can restore/recover – they cannot do it quickly or without the intervention of expert personnel. This creates serious bottlenecks and often results in hidden costs, delays, and risks,” claims Alex Yevtushenko, CEO at Salvador Technologies. “The need of a recovery solution that is both OT-centric and can provide operational continuity should be a top priority for every OT/ICS cybersecurity professional.”
While progress has been made in this regard, the report went on to assess that there still is a considerable shift that needs to occur in order to put OT/ICS recovery in the hands of the OT sector.
Sponsored by Salvador Technologies, a provider of technological solutions for operational continuity and cyber-attack recovery for ICS and OT environments, the TPR survey collated data from over 100 industrial managers, experts, and leaders across companies to disclose what they are doing in terms of recovery from a cyber incident. It gives an inside scoop on what OT/ICS cybersecurity professionals think about cyber-attack recovery in general, and in terms of their own industrial enterprise.
The survey results also found that 78 percent of respondents anticipate their OT/ICS business to be hit by a ransomware attack, leading to organizations having to respond and recover and should have a cyber-attack recovery plan in place. These responses also believe that their company’s production will fall victim to a ransomware attack over the next 12-to-24-month timeframe.
Hands-on Effect of Ransomware in OT/ICS environments
Ransomware is on the rise in OT environments and becoming ever more disruptive, leading to more damage and downtime, apart from larger ransom that adversaries can demand from their victims. A key highlight of these ransomware hackers is that they are always upping their game and improving their methods. In recent years, they have demonstrated their growing ability to get nearer to OT/ICS technologies, as showcased in the Colonial Pipeline breach, causing energy outages along the East Coast of the United States last May. Additionally, ransomware attackers nearly shut down the power grid of Queensland’s CS Energy in Australia last November.
The TPR Survey Report also noted that despite paying the ransom amount, there is no guarantee that the cybercriminals will honor their end of the bargain. While some may argue that every ransom payment becomes an incentive for criminals to attack, again and again, it is clear that industrial enterprises need a better way out of the ransomware trap and the specter of OT downtime.
More Survey Findings
The TPR Survey Report provides the inside scoop on what OT/ICS cybersecurity professionals think about cyber-attack recovery in general, and in terms of their own industrial enterprise. Since a high percentage of respondents are members of an OT or Plant cybersecurity team, their experience and insight provide valuable and highly germane perspectives on the state of cyber-attack recovery in industrial enterprises.
The results also come in at a time when there’s a growing consensus that no organization can detect or prevent all attacks. Thereby, pressurizing every organization to have a recovery plan for ‘the moment after’ a breach occurs. The existing threat landscape places industrial enterprises in an extremely precarious position, as their mission-critical operations must run 24/7 non-stop, and are extremely averse to downtime. Unplanned disruptions to water delivery, electricity distribution, oil/gas pipelines, chemical processing, manufacturing production lines, etc. can be devastating in numerous ways.
Over 60 percent of respondents have confessed that their current cyber-attack recovery plan does not adequately support OT/ICS environments, while 63 percent said that they are not confident in their cyber-attack recovery plan (i.e., business continuity) for critical OT workstations and machines. Furthermore, the TPR Survey Report added that while OT downtime can be devastating, only 22 percent of respondents aim for a recovery time of minutes or less. The expectation that recovery ‘takes time’ may be the result of underinvestment in OT attack recovery strategies and solutions.

The survey also found that only 10 percent of respondents perform continuous or weekly validation of OT workstation/system backups and restoration. Most verify their OT backups once a year or once a quarter because the process is so invasive and time-consuming.
Sixty-nine percent of respondents think that hours or days are an optimal Recovery Time Objective (RTO). Hours or days may be acceptable for recovering a single or a few workstations. However, when numerous workstations in a production environment are down, it can take several days or weeks to restore them all.
The TPR Survey Report said that while many OT people think the IT recovery team has a handle on this, most IT professionals don’t understand the complexities of the OT environment. “When we consider attack recovery time across an entire factory/site, unexpected hurdles and hidden costs often arise. In OT environments where downtime can be devastating, why do only 22% think an optimal RTO should be minutes or less? Could it be that days or weeks is the best their current solutions can do, so they don’t think it is realistic to aim for less?” it added.
Evidently, the TPR Survey Report findings reveal that industrial enterprises may be living with a false sense of security. The data will be of particular interest to OT cybersecurity teams seeking cybersecurity solutions that are designed for the needs of OT/ICS environments. The survey results will also prove that corporate cybersecurity teams who traditionally hail from the IT side of networking and tend to oversee incident recovery efforts, will find this survey report of great interest.
Cyber-attack recovery in OT/ICS environments
The TPR Survey Report calls attention to the fact that in industrial environments, OT/ICS teams must play a role in cyber-attack recovery, as the IT and cloud experts are not very mindful of the continuity of critical industrial processes, within the shortest possible time. While cloud backup and recovery solutions have made great strides in efficiency, the cloud can become a bottleneck when an entire plant or OT production line needs to be restored.
To a vast extent, a harmonious approach is the best way to align the cyber-attack recovery expectations of management with the reality of the OT production environment. OT and IT teams must work together and share the responsibility for Attack Recovery because a one-sided approach will only achieve a false sense of security.
Adopting available resources for recovery
Given the TPR Survey Report, solutions for cyber-attack recovery are gaining importance and recognition for the critical role they play in avoiding downtime after an attack and getting industrial operations fully back on track. While recovery is included in the NIST (National Institute of Standards and Technology) Cybersecurity Framework (CSF), the ‘recovery’ function has been woefully under-invested in favor of preventative measures.
The NIST CSF has been conceived by IT security experts as a guideline, with adherence usually proving helpful, though it remains entirely voluntary by nature. Traditionally, CISOs have focused their budgets on the prevention pillars of the cybersecurity framework (i.e., Identify, Protect and Detect) with the aim of building defenses that could not be breached. But, in the hacker game of ‘cat and mouse,’ it’s only a matter of time until an attack is successful. Thus, industrial organizations must work towards pitting their organizational offense a step ahead of the defense. Therefore, incident recovery is critical, especially in the industrial sector.
The potential to wreak havoc and extort large payouts makes industrial enterprises an attractive target for ransomware, political sabotage, and other attacks both internal and external. Additionally, in OT/ICS environments, breaches and damage caused by employee mistakes and lapses are often extremely damaging and difficult to fix. It is folly to depend on incident prevention measures alone.
As industrial organizations cannot afford any downtime, they must be better prepared for when things go wrong. When OT systems are breached, those who are not prepared risk harmful impacts on their business including immediate costs and projected losses from the disruption to OT/ICS operations, production lines, etc., direct costs of attack remediation and downtime recovery, the straight charge of ransomware payments, or rise in premiums if insurance has to pay. Furthermore, industrial enterprises must also bear indirect expenses resulting from litigation and or regulatory fines, apart from facing breach and potential disclosure of sensitive company data, and brand and reputation damage.
Adopting TPR’s Maturity Model for Incident Resilience
The bulk of OT-centric cybersecurity activity happens in the Recovery phase
To build up and strengthen industrial attack readiness and resilience, the TPR Survey Report directed OT/ICS environments to adopt the Maturity Model for Incident Resilience, developed by TP Research.

The model plots IT-centric versus OT-centric backup-and-restore processes in terms of the NIST CSF, in terms of the time or velocity with which these processes can be accomplished. Predominantly built to identify the stark differences in the goals and tools sets for business recovery in IT compared to the OT environments, the TPR Maturity Model brings focus on the OT requirements with regards to recovery, particularly in the case of ransomware, compared to IT environments.
The TPR Maturity Model is conscious of the fact that preparing an actual recovery plan can be tricky, especially across critical infrastructure and industrial environments. The approach proposes that they are separated from corporate IT and cloud networks using complex segmentation and air-gapping schemes, in a quick and efficient manner.



Comments